HappyMod vs Aptoide: Safety Comparison [2026]
You are looking for a way to manage apps that are not available on the standard Google Play Store. You might be researching how modified versions of games behave compared to the original versions.
Two names always come up: HappyMod and Aptoide. At first glance, they look like the same thing. But my security tests show they are built very differently. One is a curated utility for verifying modified files; the other is an open marketplace where anyone can upload files. I compared their security architectures to help you understand the risks.
Part of our Security Comparisons series.
Core Focus: The Main Difference
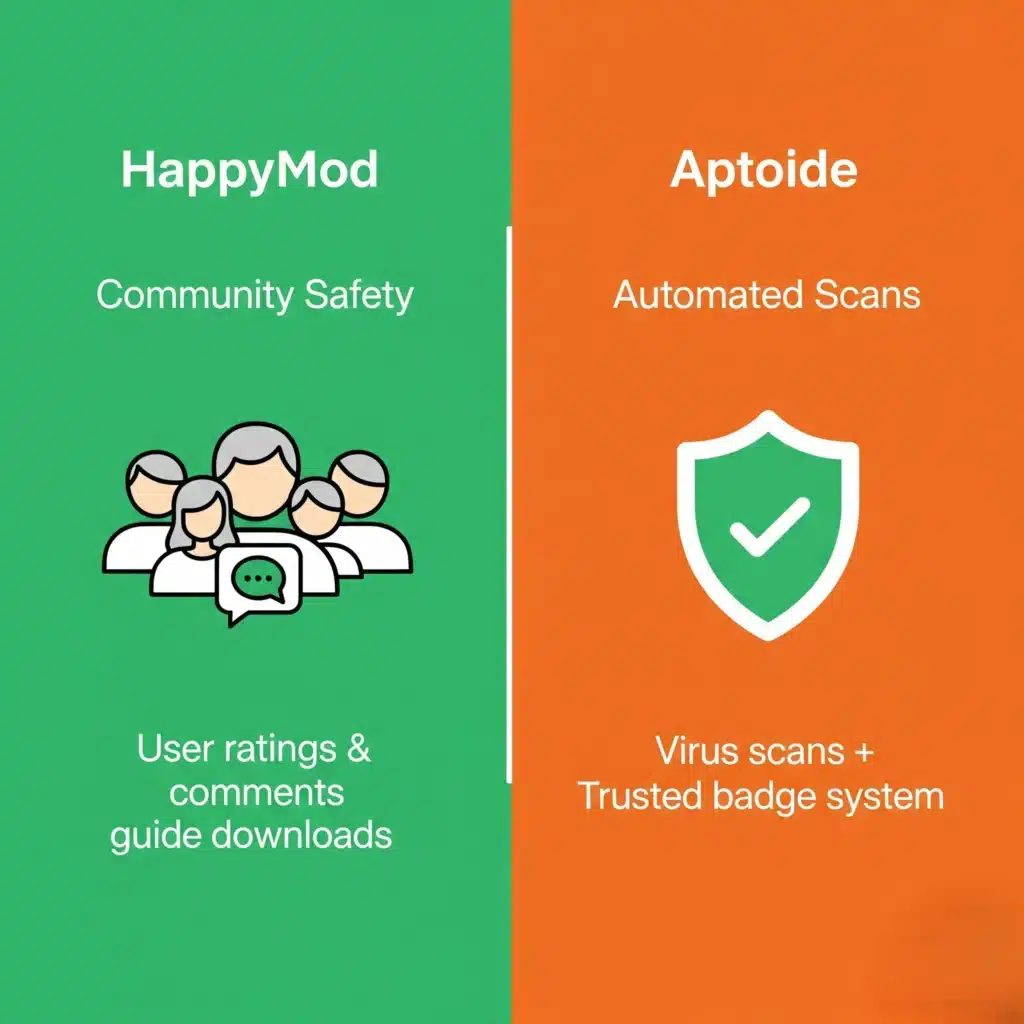
HappyMod
When I analyze HappyMod, I look at it as a Management Tool. Its purpose is not just to list apps, but to categorize specific modifications (like altered game physics or unlocked regions) and verify if they are safe to execute. It focuses strictly on the “Modified” ecosystem.
Aptoide
Aptoide functions as a massive alternative to the Play Store. It hosts millions of standard apps. However, it allows users to create their own “Stores.” This means you are often downloading a file from a stranger’s personal repository, not a central server.
Analyst Technical Note:
The architectural distinction is Centralized vs Decentralized.
- HappyMod uses a Curated Chain of Custody. Files are reviewed against a threat database before being indexed.
- Aptoide operates as a P2P Hybrid Marketplace. It allows user generated binaries. This creates a Supply Chain Vulnerability where malicious actors can clone legitimate apps, inject code, and upload them to their personal store.
Head to Head Comparison
To make the choice clearer, I have put the main points into a simple chart. It shows how HappyMod and Aptoide stack up against each other in four important areas.
| Feature | HappyMod Ecosystem | Aptoide Marketplace |
| Primary Utility | Mod Verification | App Repository |
| Security Model | Centralized Audit | Decentralized Scan |
| Risk Class | 🟢 Low | 🟡 Medium |
| Adware Vector | Low (Strict Protocol) | Medium (User Uploads) |
| Analyst Rating | High | Low |
Compare a massive software library in our full HappyMod vs Softonic review.
Security Protocols
How HappyMod Filters Threats
The HappyMod ecosystem uses a “Crowdsourced + Forensic” approach.
- Telemetry: The utility tracks user reports to identify instability immediately.
- Manual Review: High-traffic files are often subject to manual review.
- Transparency: The utility displays the Verification Ratio (Safety Score) next to the file, so users can see the risk data before proceeding.
You can learn more about our multi step verification process in our Safety & Security Pillar.“
How Aptoide Filters Threats
Aptoide uses an automated “Trusted” badge system. If an app passes their virus scan, it gets a green shield. However, automated scanners often miss “Logic Bombs” or new malware variants. Because the upload volume is so high, infected files can exist on the platform until a user reports them.
Security Warning
Aptoide’s decentralized model suffers from “Repackaging Attacks.” A bad actor can download a clean app (like WhatsApp), inject a payload, and re-upload it. Since Aptoide hosts thousands of duplicate versions of the same app, users can sometimes select a compromised version by mistake.
Which Utility Fits Your Needs?
My choice between these two always depends on what I need to do. Here is how I decide which one to open.
Use HappyMod If…
- You are researching Modified Software Behavior (e.g., Sandbox environments).
- You require a file that has undergone Manual Integrity Verification.
- You want to reduce the risk of user uploaded malware.
Read more: How to Avoid Malicious Apps & Fakes
Use Aptoide If…
- You need to rollback to an Older Version of a standard application (e.g., for compatibility testing).
- You are looking for standard, unmodified Android packages.
- Advisory: Strictly limit downloads to items with the Green ‘Trusted’ Shield. For added security, run any file through our Online Virus Scanner before executing.
Final Safety Verdict
If your goal is to analyze or utilize modified Android packages, the HappyMod Utility offers a more controlled security environment due to its centralized verification logic. Aptoide remains a valid option for standard app archival, but its open structure introduces higher variables of risk.
Do not execute unverified binaries. Use the original management tool to audit file safety. You can review the HappyMod utility on TheHappyMod.com for research and testing purposes.
People Also Ask
Why does HappyMod flag files that Aptoide marks as “Safe”?
This is a difference in Heuristic Sensitivity. Aptoide’s automated scanners often look for known virus signatures (e.g., Trojan.Gen). My audit process at HappyMod looks for Behavioral Anomalies—such as an app requesting “Admin Permissions” or “SMS Access” when it shouldn’t. A file might be “virus-free” but still invade your privacy; our goal is to flag those privacy risks.
Does Aptoide or HappyMod require Root Access?
No. Both utilities function within the standard Android Application Sandbox. HappyMod does not require root access to function. While some advanced users may use root based tools for controlled research purposes, standard users should remain within the Android application sandbox to reduce security risks.
Why are download speeds different between the two platforms?
This is an infrastructure difference. Aptoide uses a P2P-style distribution (Peer-to-Peer), where you might be downloading data from various nodes. HappyMod uses a centralized verification index to ensure file integrity before files are listed in the ecosystem. While P2P can be faster, Centralized Hosting allows for stricter security verification (Checksum Validation) before the file reaches your device.

Jonathan Jude – Mobile Security Analyst & APK Reviewer
Based in Los Angeles, Jonathan Jude has four years of hands on experience reviewing Android apps and mobile software. He writes clear, technical articles focused on app behavior, safety signals, and common user risks.
His work centers on a documented testing process that checks file integrity, permissions, and real world performance. This helps readers understand potential risks before installing third party software. You can connect with Jonathan Jude on LinkedIn and Facebook.